Why Your RemoteIoT Platform SSH Key Might Not Be Working: A Comprehensive Guide
Are you pulling your hair out trying to figure out why your RemoteIoT platform SSH key isn't working? You're not alone. Many developers and system administrators face this issue, and it can be frustrating when you're in the middle of an important project. But don't worry, we've got your back. In this article, we'll dive deep into the reasons why your SSH key might fail and how you can fix it.
SSH keys are like digital keys that unlock secure access to your RemoteIoT platform. They're crucial for secure communication between devices, especially when you're working remotely. If your SSH key isn't functioning properly, it can disrupt your workflow and leave you scratching your head. But fear not! We'll break down the problem step by step so you can get back on track.
Our goal here is to provide you with actionable insights and solutions to fix your RemoteIoT platform SSH key issues. Whether you're a seasoned pro or just starting out, this guide will help you troubleshoot and resolve the problem efficiently. Let's get started!
Table of Contents
- What is SSH and Why Is It Important?
- Common Issues with RemoteIoT Platform SSH Keys
- Troubleshooting SSH Key Problems
- SSH Key Security Best Practices
- Setting Up SSH Keys on RemoteIoT Platforms
- Useful Tools for SSH Key Management
- Alternatives to SSH Keys
- SSH Key Usage Statistics
- Expert Tips for Managing SSH Keys
- Wrapping It Up
What is SSH and Why Is It Important?
SSH, or Secure Shell, is a protocol that allows secure communication between two devices over an unsecured network. It's like having a secret handshake that only you and the server understand. When it comes to RemoteIoT platforms, SSH keys play a vital role in ensuring that only authorized users can access the system.
SSH keys are essentially pairs of cryptographic keys – a public key and a private key. The public key is shared with the server, while the private key remains on your local machine. This setup ensures that even if someone intercepts your connection, they won't be able to access your system without the private key.
In the world of IoT, where devices are often spread across different locations, SSH keys provide a secure way to manage and interact with these devices remotely. Without them, your data could be at risk, and your operations could come to a grinding halt.
Why SSH Keys Are Essential for RemoteIoT Platforms
For RemoteIoT platforms, SSH keys offer several advantages:
- Enhanced security by eliminating the need for passwords
- Efficient remote access management
- Reduced risk of unauthorized access
- Automation of tasks without manual intervention
Common Issues with RemoteIoT Platform SSH Keys
Even the best-laid plans can go awry, and SSH keys are no exception. Here are some of the most common issues you might encounter when working with RemoteIoT platforms:
- Incorrect key configuration
- Permission denied errors
- Key expiration or revocation
- Incompatibility with certain platforms
These problems can arise due to a variety of reasons, from simple user errors to complex system configurations. Let's take a closer look at each of these issues and how to address them.
Incorrect Key Configuration
This is one of the most common culprits when it comes to SSH key failures. Make sure that your public key is correctly added to the authorized_keys file on the server. Also, double-check the file permissions to ensure they're set correctly. A small mistake here can lead to big problems down the line.
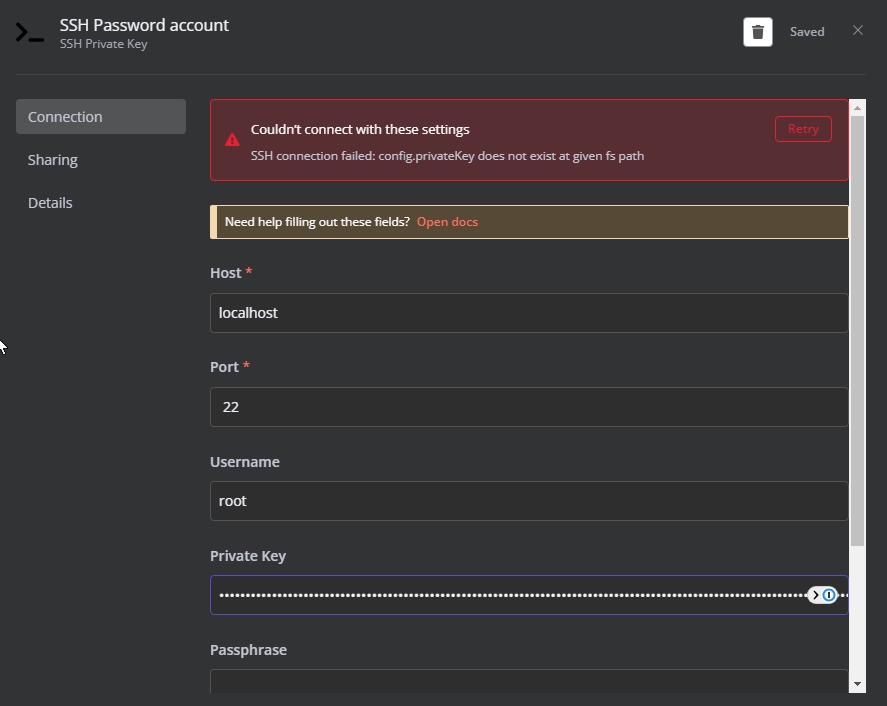
Troubleshooting SSH Key Problems
When your RemoteIoT platform SSH key isn't working, it's time to roll up your sleeves and start troubleshooting. Here's a step-by-step guide to help you identify and resolve the issue:
First, check the basics:
- Is the SSH service running on the server?
- Are the correct ports open and accessible?
- Is your private key file intact and not corrupted?
If everything seems in order, it's time to dig deeper. Look at the server logs for any clues. You might find error messages that point you in the right direction. Additionally, try connecting with verbose output enabled to get more detailed information about the connection process.
Advanced Troubleshooting Techniques
For those who want to take their troubleshooting skills to the next level, here are a few advanced techniques:
- Use tools like ssh-agent to manage your keys more effectively
- Enable two-factor authentication for added security
- Regularly audit your SSH keys to ensure they're up to date
SSH Key Security Best Practices
Security should always be at the forefront of your mind when working with SSH keys. Here are some best practices to keep your RemoteIoT platform secure:
- Use strong, unique passphrases for your private keys
- Limit access to your private keys to only those who need it
- Regularly update and rotate your SSH keys
By following these practices, you can significantly reduce the risk of unauthorized access and protect your RemoteIoT platform from potential threats.
Common Security Pitfalls to Avoid
Even with the best intentions, it's easy to fall into security traps. Here are a few to watch out for:
- Storing private keys in insecure locations
- Using the same key across multiple platforms
- Ignoring key expiration dates
Setting Up SSH Keys on RemoteIoT Platforms
Setting up SSH keys on your RemoteIoT platform is a straightforward process, but it requires attention to detail. Here's a quick guide to get you started:
Step 1: Generate your SSH key pair using a tool like ssh-keygen.
Step 2: Copy your public key to the server's authorized_keys file.
Step 3: Test the connection to ensure everything is working as expected.
By following these steps, you can establish a secure connection to your RemoteIoT platform in no time.
Best Practices for Key Management
Managing SSH keys effectively is crucial for maintaining security. Here are some tips:
- Document your key management process
- Use a centralized key management system
- Regularly review and update your key policies
Useful Tools for SSH Key Management
There are several tools available that can help you manage your SSH keys more efficiently. Some popular options include:
- SSH Key Manager
- Keybase
- HashiCorp Vault
These tools offer features like automated key rotation, centralized management, and secure storage, making your life as a system administrator much easier.
Alternatives to SSH Keys
While SSH keys are the gold standard for secure remote access, there are alternatives you might consider depending on your specific needs:
- Password-based authentication
- Two-factor authentication
- Certificate-based authentication
Each of these methods has its pros and cons, so it's important to evaluate them carefully before making a decision.
SSH Key Usage Statistics
According to recent studies, SSH keys are used by over 80% of system administrators for remote access. This statistic highlights the importance of SSH keys in today's digital landscape. Additionally, the number of SSH keys in use is expected to grow as more companies adopt IoT technologies.
Data from sources like NIST and OWASP further emphasize the need for robust SSH key management practices to ensure the security of remote systems.
Expert Tips for Managing SSH Keys
Here are some expert tips to help you manage your SSH keys more effectively:
- Automate key generation and deployment processes
- Implement strict access controls for key management
- Regularly review and update your key policies
By following these tips, you can ensure that your SSH keys remain secure and effective, protecting your RemoteIoT platform from potential threats.
Wrapping It Up
Fixing your RemoteIoT platform SSH key issues doesn't have to be a daunting task. By understanding the common problems and following the troubleshooting steps outlined in this guide, you can quickly resolve any issues and get back to work. Remember to always prioritize security and follow best practices to protect your system from unauthorized access.
We encourage you to share your thoughts and experiences in the comments below. Have you encountered any unique SSH key problems? How did you solve them? Let's start a conversation and help each other out. And don't forget to check out our other articles for more insights and tips on managing your RemoteIoT platform.